clickjack_check
巩固写代码,顺便使用loguru记录日志emmm;此处本质上就是检测返回数据包中是否存在X-FRAME-OPTIONS
废话不说,直接上代码
非面向对象
1 | import requests |
面向对象
1 | import requests |
效果如图:包含日志信息(日志信息如果想只存储结果,格式化时只保留message即可)
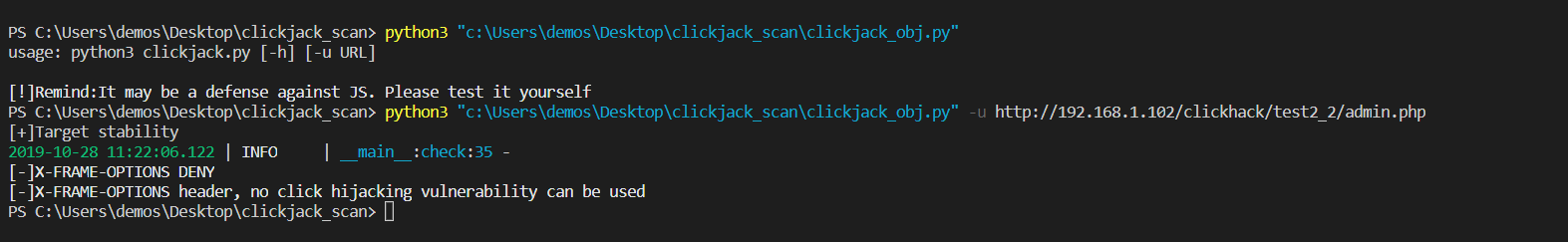
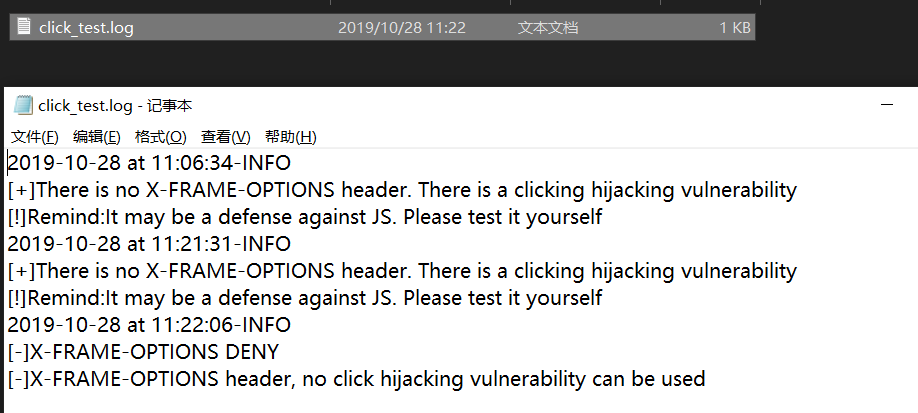
关于loguru可以看之前的文章
It's A Long Road
巩固写代码,顺便使用loguru记录日志emmm;此处本质上就是检测返回数据包中是否存在X-FRAME-OPTIONS
废话不说,直接上代码
1 | import requests |
1 | import requests |
效果如图:包含日志信息(日志信息如果想只存储结果,格式化时只保留message即可)


关于loguru可以看之前的文章